Product Version: 6.5.x.x
Overview
Saner CVEM provides comprehensive endpoint management and vulnerability assessment capabilities. The Organization Canned Reports offer detailed insights into device compliance, patch management, and vulnerability posture across all managed endpoints. These reports help organizations monitor risks, prioritize remediation activities, and assess the impact of patch deployments, enabling informed security decision-making at both account and organizational levels.
The reports are categorized into three primary types:
Organization Risk Assessment Report
Organization Risk Prioritization Report
Organization Patch Impact Report
Each report serves a specific purpose in managing endpoint security effectively.
How to Access the Reports
You can easily access the Organization Canned Reports from the Saner CVEM dashboard by following the steps below:
Log in to the Saner CVEM Console using your credentials.
Click on the three-line (☰) menu icon at the top-left corner of the dashboard.
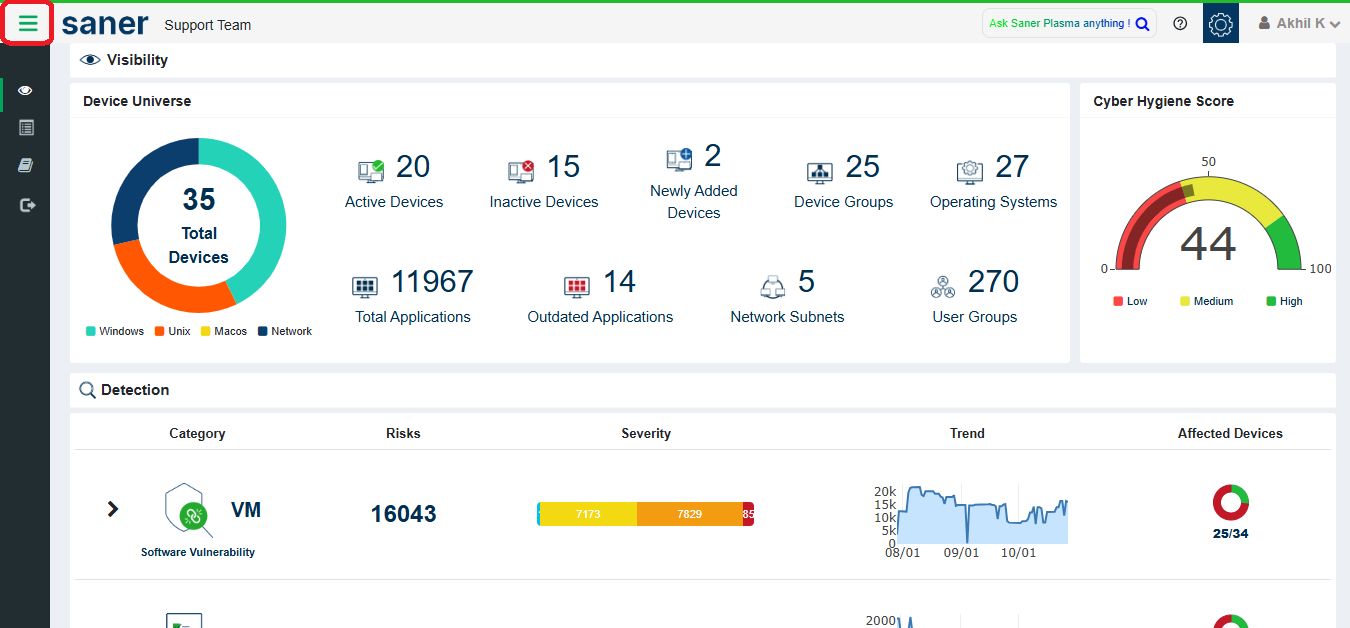
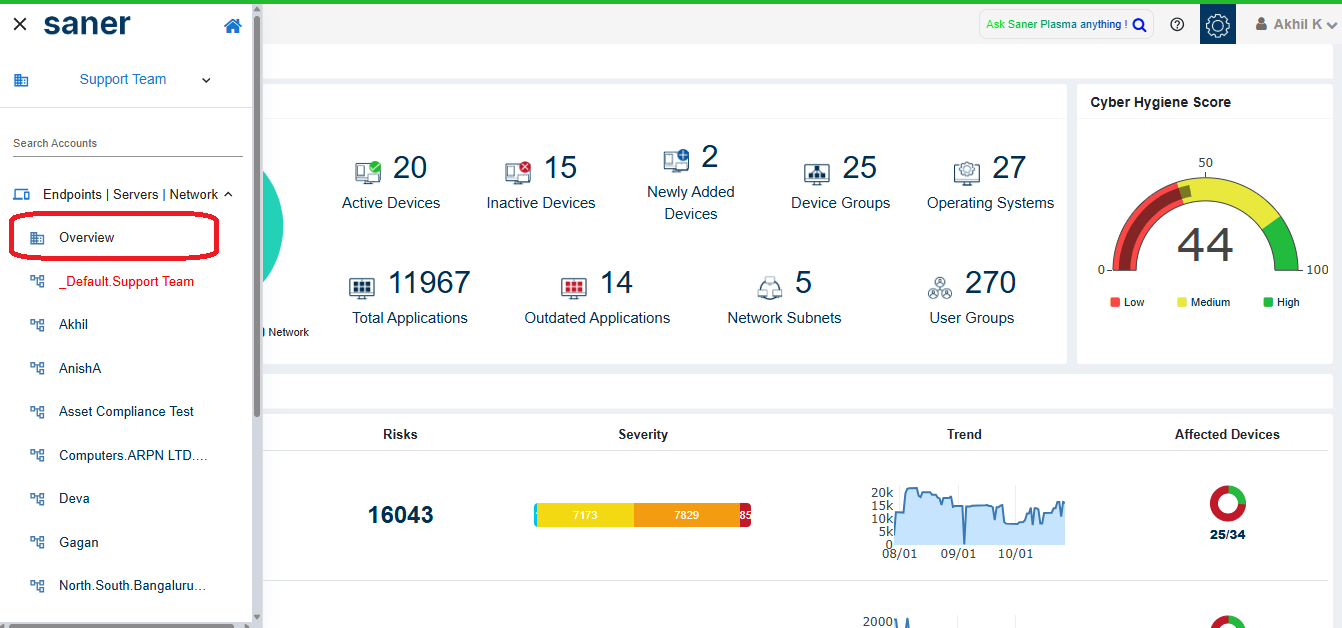
Select Overview from the menu options.
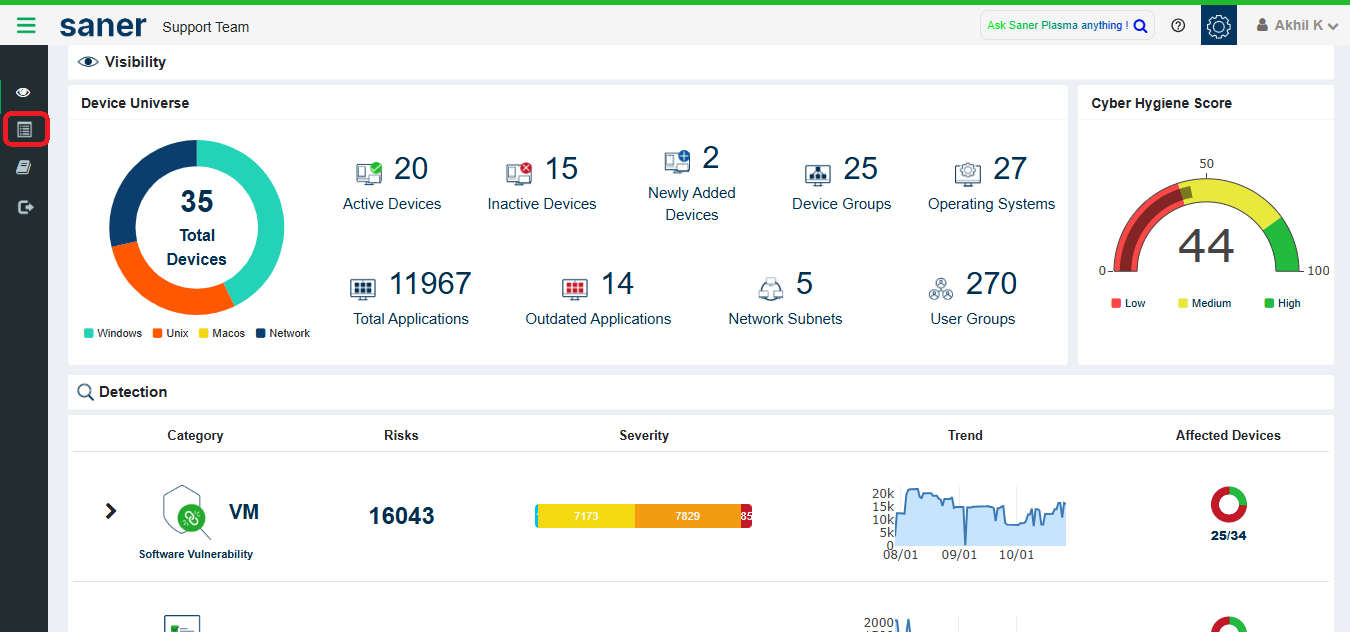
Click on the Reports tab.
Navigate to the Saved Reports section.
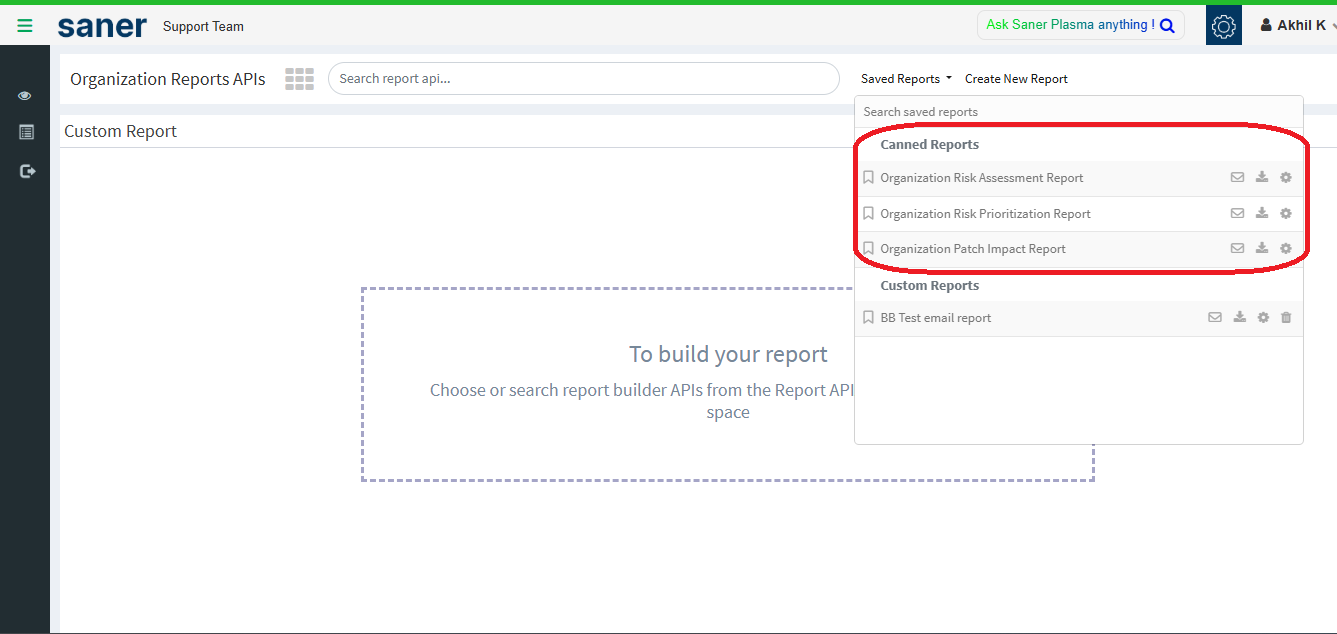
Here, you can view and download all the Canned Reports (predefined organizational reports).
These reports provide summarized and detailed information about risk exposure, vulnerability severity, and patch management activities across the organization.
Report 1: Organization Risk Assessment Report
The Organization Risk Assessment Report provides a comprehensive view of all devices under management, their operational status, and overall endpoint compliance. It highlights:
Total number of devices, active and inactive endpoints, and devices that are up-to-date.
Account-wise device distribution for total, active, inactive, and compliant devices.
Missing security patches across devices and their severity (Critical, High, Medium, Low).
Device family segmentation (Windows, Linux, macOS, etc.) for better risk visibility.
This report helps identify inactive endpoints and accounts with higher security risks, enabling proactive device management and risk mitigation.
Report 2: Organization Risk Prioritization Report
The Organization Risk Prioritization Report focuses on identifying and prioritizing vulnerabilities and missing patches based on risk levels. It provides:
Severity-wise breakdown of missing patches and open vulnerabilities.
Account and device family–based patch information.
Patch aging insights showing how long patches have been pending.
Details of top vulnerable devices and high-risk patches requiring immediate attention.
Information about manual patches and end-of-life operating systems.
This report enables administrators to prioritize remediation efforts and address the most critical risks first.
Report 3: Organization Patch Impact Report
The Organization Patch Impact Report focuses on the effectiveness of patch deployment and the resulting risk reduction. It includes:
Total patches applied and risks mitigated organization wide.
Trend charts for installed security patches and vulnerabilities identified in the last 90 days.
Summary of patch tasks (successful, failed, and ongoing).
Details of patch failures and root causes (dependencies, permission issues, or missing binaries).
Risk mitigation summary categorized by severity (Critical, High, Medium, Low).
This report helps assess patch performance, track remediation success rates, and evaluate the impact of patching on overall organizational security.
Conclusion
The three reports—Organization Risk Assessment, Risk Prioritization, and Patch Impact—together provide a holistic overview of your organization’s endpoint security posture. They enable you to:
Monitor device compliance and operational health.
Prioritize vulnerabilities based on risk severity.
Evaluate patch deployment success and overall risk reduction.
By regularly reviewing these reports, organizations can maintain stronger endpoint security, ensure timely patching, and make data-driven security decisions.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article