Product Version: 6.5.x.x
Overview
This article explains how to identify vulnerability severity levels (Low, Medium, High, Critical) for installed applications in Product Version 6.5.x.x. It also provides detailed guidance on generating vulnerability and patch compliance reports that help assess the security posture of endpoint devices.
Purpose
Identify vulnerability severity for installed software
Track missing patches for known vulnerabilities
Generate status reports for risk analysis and remediation planning
Vulnerability Severity Levels
The platform categorizes vulnerabilities into the following severity levels based on vendor advisories and CVSS scoring:
| Severity Level | Description |
|---|---|
| Low | Minimal impact, unlikely to cause exploitation |
| Medium | Moderate impact, possible exploitation under specific conditions |
| High | Significant impact, high likelihood of exploitation |
| Critical | Severe impact, immediate remediation required |
Recommended Reports
Use the built-in reporting features to gather vulnerability and patch status information. The following reports will help meet compliance and security visibility requirements:
1️. Third-Party Security Patches Report
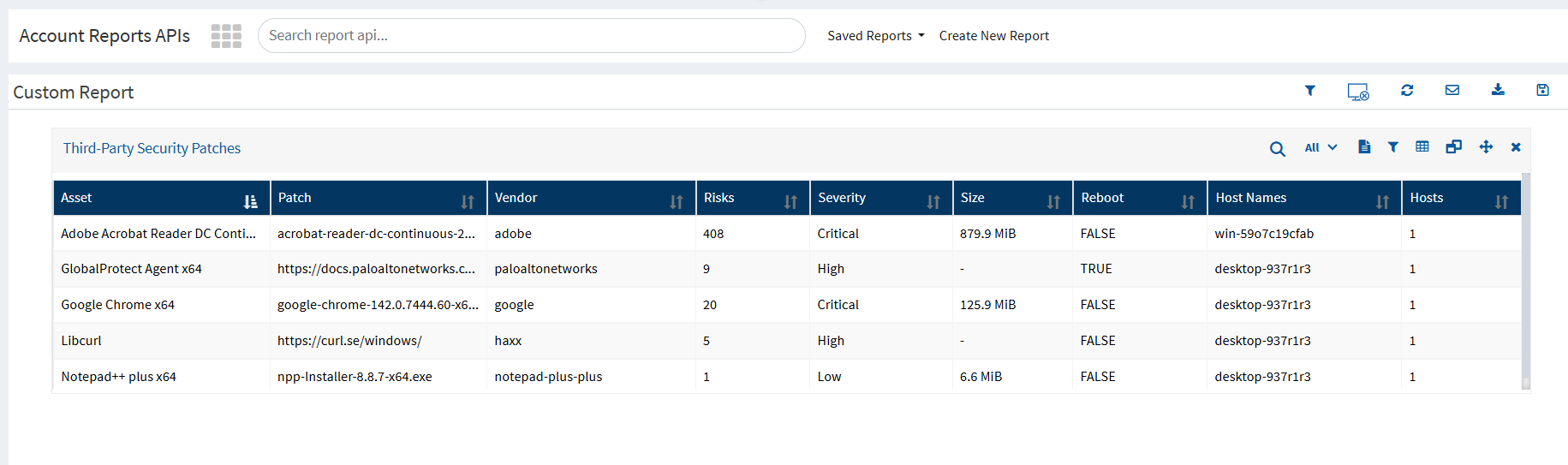
Shows missing security patches for third-party applications
Helps identify vulnerabilities affecting installed software
Useful for prioritizing patch deployment
Report Output Includes:
Device details
Application name and version
Missing patch severity (Low/Medium/High/Critical)
2️. Vulnerabilities With Patches Report
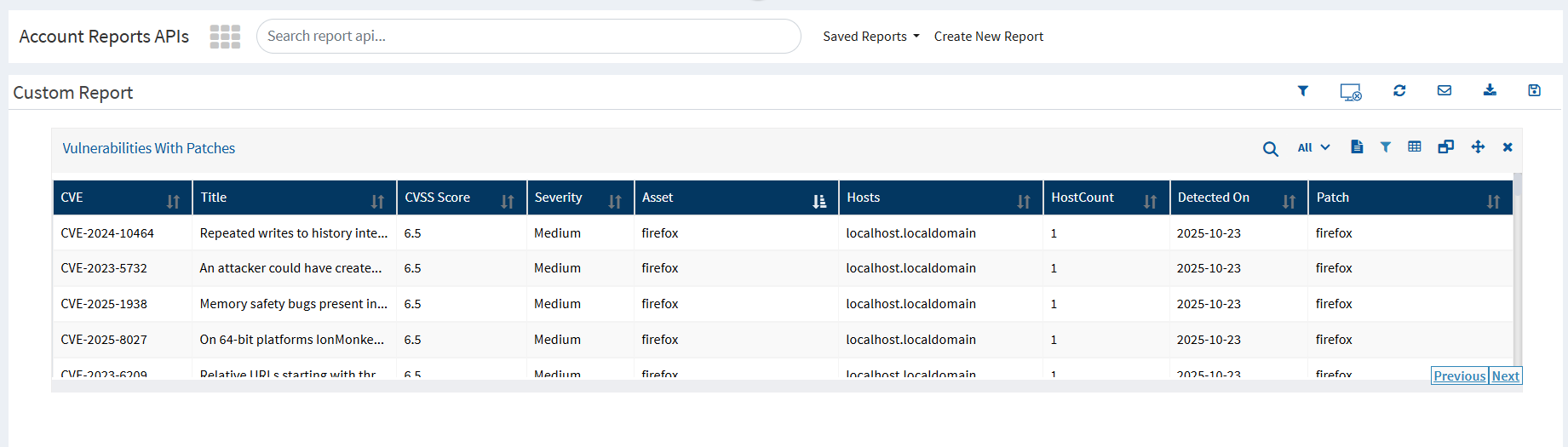
Displays assets with known vulnerabilities that have patches available
Helps track the number of risks per device or application
Supports targeted remediation planning
Report Provides:
Vulnerable application details
Associated CVE/CVSS information
Patch availability status
3️. Installed Patches by Devices Report
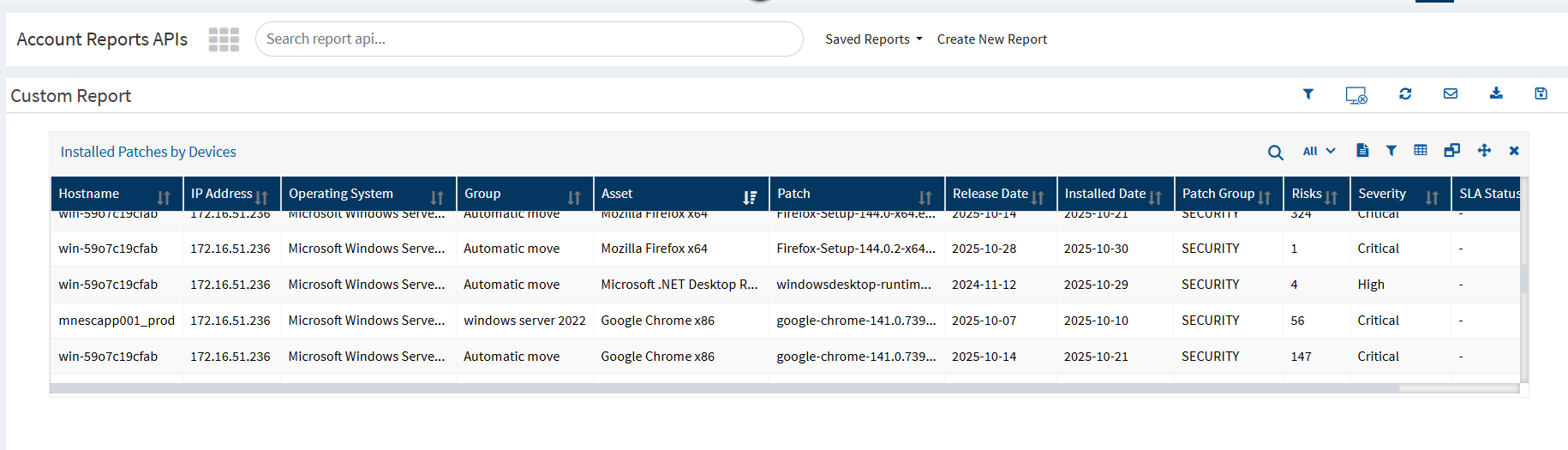
Lists successfully installed patches across endpoints
Helps validate remediation efforts and compliance status
Report Contains:
Device-wise patch installation summary
Patch classification (Security / Non-Security)
Installation status and timestamps
How to Generate Reports
Log in to the Console with appropriate administrator permissions
Navigate to Reports → Patch Management / Vulnerability Management
Select the relevant report category mentioned above
Configure filters (e.g., Severity, Device Groups, OS, Time Range)
Generate and export report in supported formats (CSV/PDF)
Recommendations
Schedule automated reporting for continuous compliance awareness
Prioritize remediation efforts focusing on High and Critical vulnerabilities
Utilize dashboards to monitor security trends and patch adoption progress
Conclusion
By using the above reporting capabilities, administrators can easily identify vulnerability severity levels for installed applications and maintain risk visibility across all managed endpoints.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article