Overview:
The Trusted Platform Module (TPM) is a dedicated security chipset embedded in modern computing devices. It provides hardware-level protection for storing sensitive information such as cryptographic keys, passwords, and certificates. TPM plays a critical role in safeguarding system integrity, enabling secure boot, and supporting features like disk encryption (e.g., BitLocker).
There are three main types of TPM implementations:
Discrete TPM (dTPM): A separate chip soldered onto the motherboard.
Firmware TPM (fTPM): Integrated into system firmware and runs within the main CPU.
Add-on TPM Modules: Optional modules that can be installed via motherboard headers.
TPM is available in two major versions:
TPM 1.2: Older, with basic functionality.
TPM 2.0: Newer, more secure, and required for Windows 11.
Common Use Cases
TPM is leveraged in various security-critical functions:
Secure Boot: Ensures only trusted software loads during startup.
BitLocker Encryption: Stores encryption keys to protect data.
Credential Protection: Works with Windows Hello and Credential Guard to protect user credentials.
Regulatory Compliance: Helps meet security standards like Windows 11 baseline, HIPAA, PCI-DSS, and GDPR.
Why TPM Is Important for Security
As cyber threats increasingly target the firmware and boot processes, TPM helps establish a trusted computing base. Here are key reasons why TPM is essential:
1. Hardware-Based Root of Trust
TPM establishes a secure foundation at the hardware level, preventing tampering from malware that could bypass software defenses.
2. Secure Key Storage
It protects cryptographic keys, ensuring they cannot be extracted even if the system is compromised.
3. System Integrity Checks
TPM validates the system’s firmware, bootloaders, and OS components during startup. Any unauthorized changes trigger security alerts or prevent the system from booting.
4. Credential Security
Credentials (PINs, biometric data) stored in TPM are isolated from the OS, making them harder to steal through malware.
5. Supports Security Compliance
TPM 2.0 is a baseline requirement for modern OS features and security compliance across many industries.
How to Check TPM Availability on Windows
You can check if your system has TPM and what version is available using the following methods:
1. TPM Management Console
- Press Windows + R, type tpm.msc, and press Enter.
- Review the TPM status and specification version.
Look for:
- “The TPM is ready for use” → TPM is active.
- Specification Version → TPM version (e.g., 2.0 or 1.2).
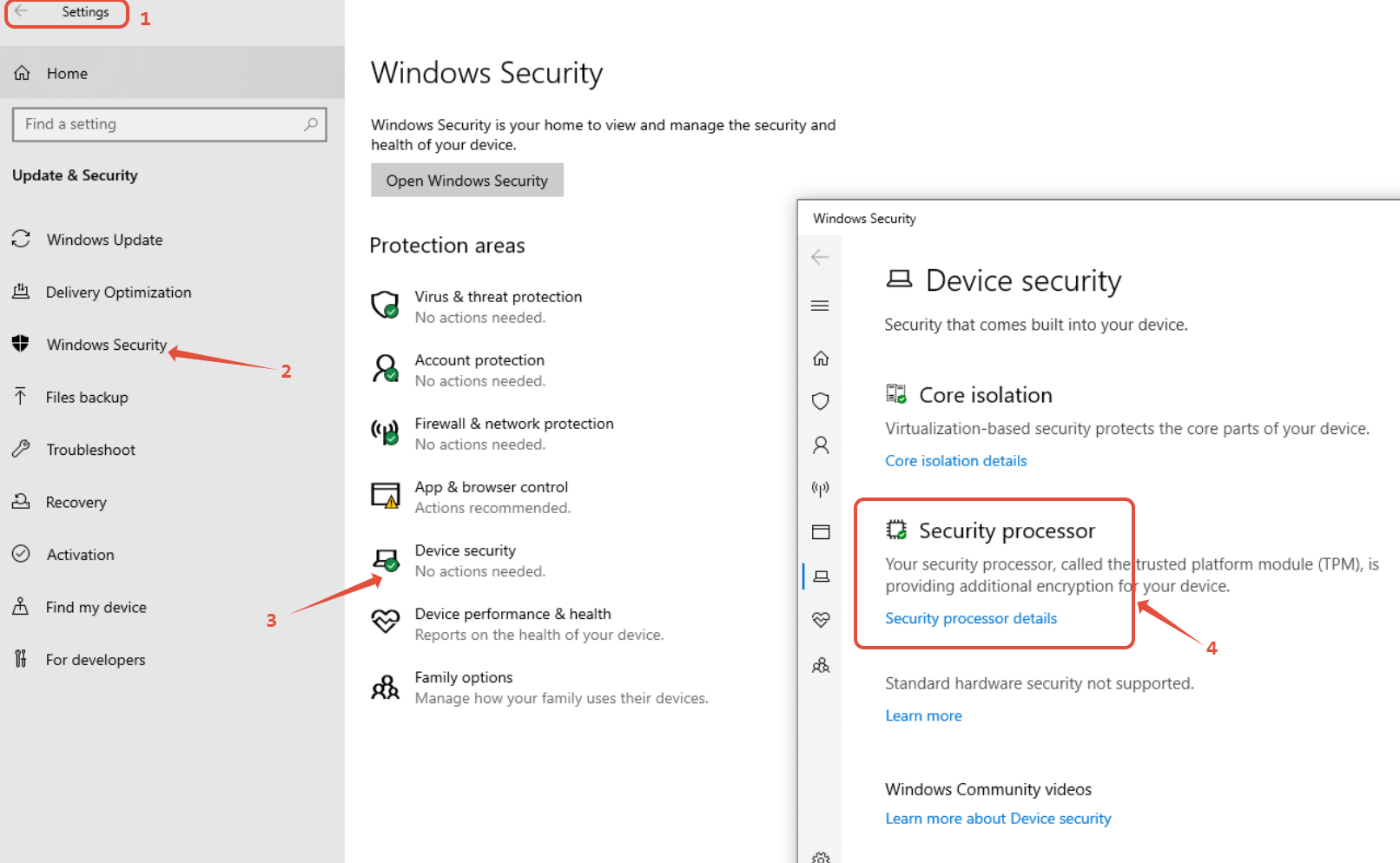
2. Windows Settings (For TPM 2.0)
Open Settings → Update & Security → Device Security.
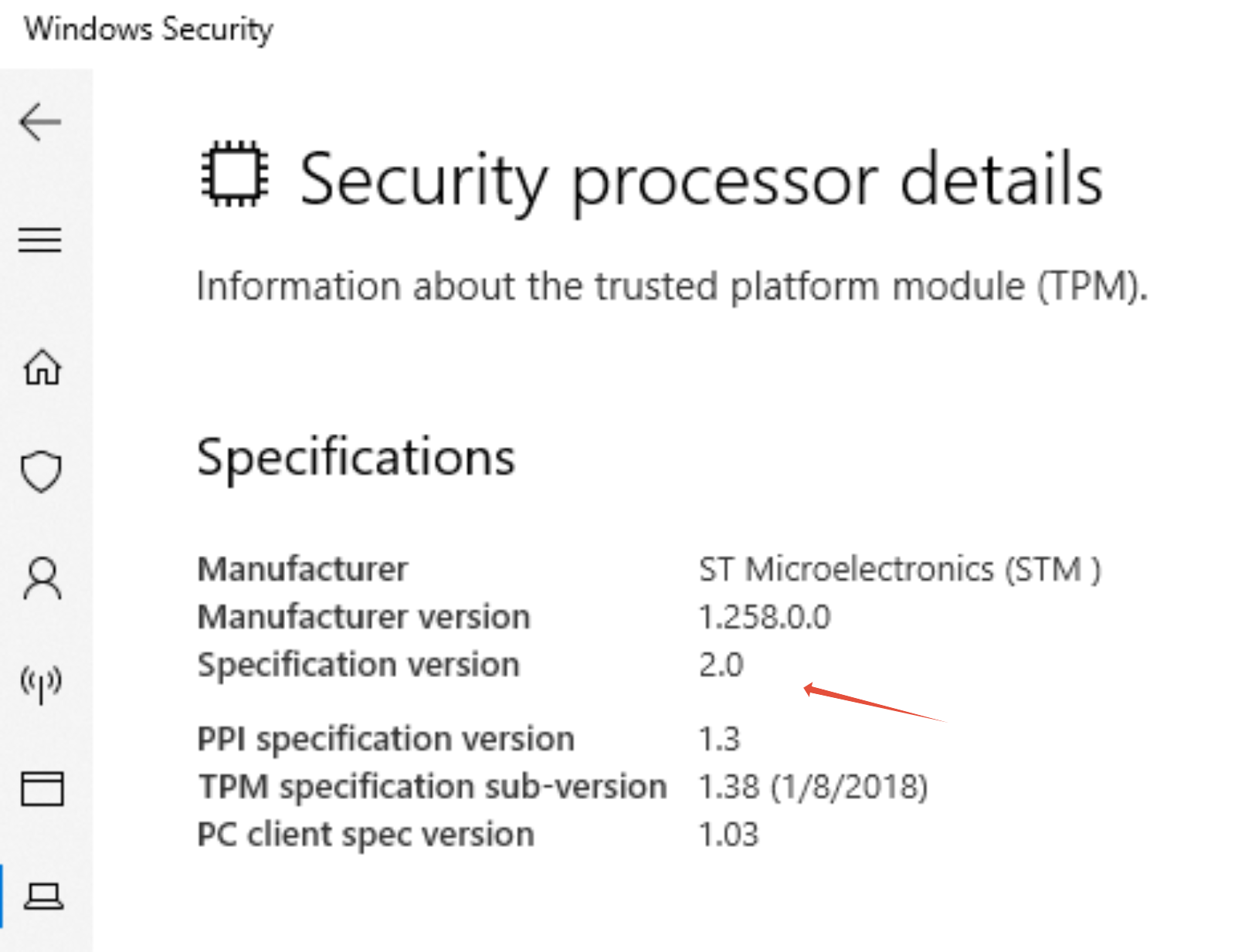
Click Security Processor Details to view TPM information.
3. PowerShell Command

Run the following command in PowerShell:
Get-WmiObject -Namespace "Root\CIMv2\Security\MicrosoftTpm" -Class Win32_Tpm
This will display:
TPM activation status
Manufacturer ID
Specification version
4. Device Manager
Open Device Manager.
Expand Security Devices.
Look for Trusted Platform Module listed.
5. Command Prompt
Use this command to check TPM version:
wmic /namespace:\\root\CIMV2\Security\MicrosoftTpm path Win32_Tpm get SpecVersion
If TPM Is Not Detected
If TPM does not appear in the methods above:
It may be disabled in BIOS/UEFI. Enable it via your system's firmware settings.
The system may not have a TPM chip (common in older hardware).
If your system supports firmware TPM (fTPM), it must be enabled in BIOS.
Conclusion:
TPM is a foundational security component that strengthens device integrity, protects sensitive data, and supports compliance with modern security standards. Verifying its presence and configuration is essential for organizations adopting Windows 11 and implementing secure computing environments.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article